HomePage » Centralized Log Management: Consolidating SOC Strategic Operation Core
- Author: TPIsoftware
Centralized Log Management: Consolidating SOC Strategic Operation Core

According to the “2024 Cisco Cybersecurity Readiness Index” report, 52% of organizations lost more than 300,000 dollars in 2023 due to cybersecurity incidents, while 12% lost more than 1 million dollars.
In the digital era, information security is an important foundation for stable operation of enterprises. Thus, many nations reinforce information security through legislation. In the case of Thailand, the Security Operations Center (SOC) is regarded as a key strategy and plays an important role in protecting information security at the individual, corporate, and national levels.
Therefore, by continuously establishing or amending strict regulations of relevant laws, such as the National Cybersecurity Act, the Payment System Act B.E. 2560 (2017), and Thailand’s Personal Data Protection Act (PDPA), it is hoped that corporate organizations can establish strong SOCs to increase alertness and respond to various threats quickly, ensuring the safety and compliance of cybersecurity.
What is SOC? 3 major functions of SOC.
The Information Security Operations Center (SOC) is a vital core of an enterprise’s information security protection. Its purpose is to prevent the enterprise from being threatened by information security attacks. The SOC integrates information security personnel, processes, technologies, and facilities, and is responsible for monitoring and analyzing the information security status of the enterprise 24/7. In the event of an information security incident, it can respond quickly and systematically to minimize the damage.
SOC includes 3 major functions:
- “Prevent” Information Security Incidents: Examine all systems, devices, and generated data of the organization, and establish corresponding information security protection measures. Develop secure communication methods, conduct periodic tests, and ensure that information security tools, including protection software and firewalls, are regularly updated to the latest versions.
- “Detect” Information Security Incidents: Utilize information security tools and technologies to monitor activities across devices, applications, servers, databases, and networks, detecting potential security threats in advance to prevent security incidents. For example, SOC typically collaborates with Security Information and Event Management (SIEM) to record and manage Log, and to automatically monitor and identify potential security risks.
- “Resolve” Security Incidents: When an organization is under an information security attack, the SOC team must promptly identify the attacked device/equipment; block, isolate, and delete infected devices and files; minimize the scope of the attack; and conduct root cause analysis (RCA) to prevent similar attacks in the future.
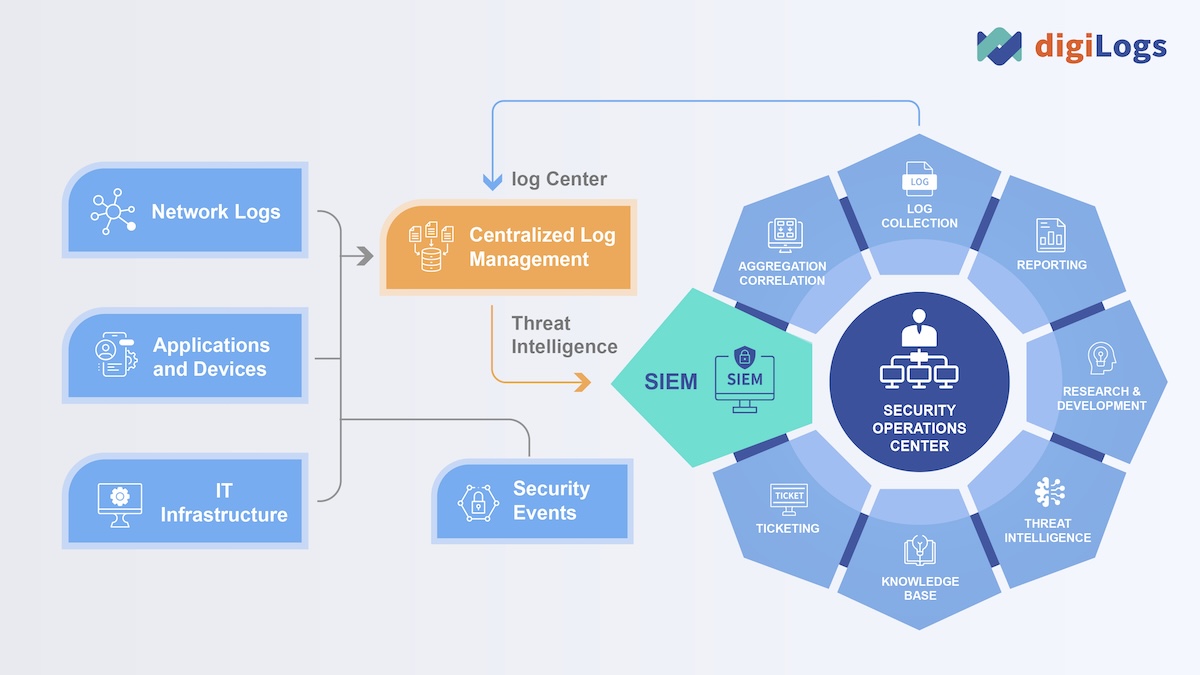
Log management plays an important role in SOC
As a crucial component of information security, Log management stores and protects log data scattered across various systems and devices in a centralized manner. It not only meets the compliance requirements but also enables SOCs to analyze data quickly and comprehensively, allowing for timely prevention of system anomalies.
Additionally, centralized Log management enhances the efficiency of “Detect” and “Resolve”. By collecting, extracting, and preserving data, it supports EDR endpoint monitoring and RCA root cause analysis, providing clues to system issues. This accelerates threat detection and response times, assists in eliminating anomalies accurately, and enhances enterprise information security protection. It proves to be a valuable asset for information security personnel.
High-Efficient Log Management to accomplish SOC strategy
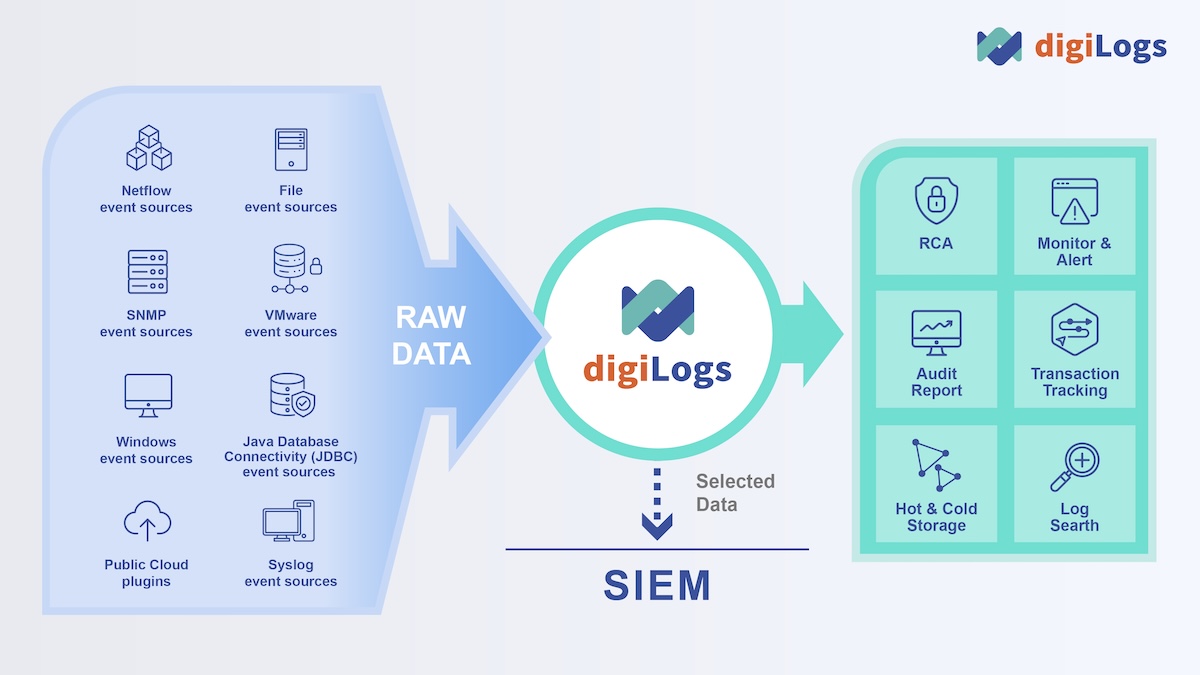
- Reducing Enterprise Costs: Effective Log collection for information security analysis can reduce the costs incurred in monitoring system activities on the Security Information and Event Management (SIEM) system.
- Avoiding Oversized Logs: The streamlining of Log data in digiLogs supports the integration of various devices and system logs. It formalizes and effectively reduces data size to ensure that the system does not exceed its storage or processing capabilities due to excessive data, and prevents the risk of system crashes due to overloading.
- Enhancing Integrated Analysis: Allowing data from different sources to be integrated and analyzed on a one-stop platform, thereby achieving greater efficiency in data analysis, and improving the quality and speed of decision-making.
- Protecting Data Integrity: Ensuring that data is securely stored on the platform and has protection mechanisms to prevent tampering, thus maintaining the integrity and usability of data. This is crucial for compliance with regulations and accurate analysis.
Enterprises should carefully evaluate and improve their organization’s log management strategies to avoid massive financial and reputational losses caused by information security attacks. If you have concerns or questions regarding information security, and want to implement SOC or deploy a centralized Log management platform, please learn more about digiLogs or contact TPIsoftware.
